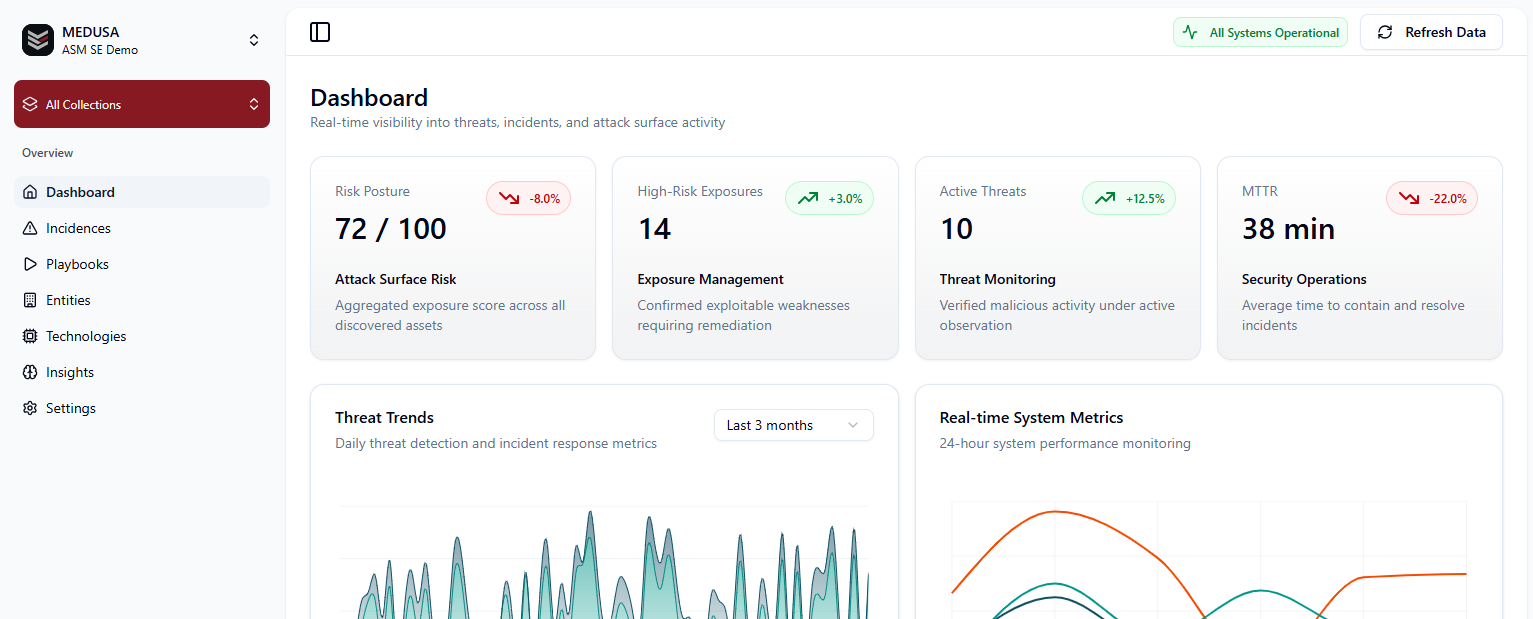
What is Medusa by SSO GROUP?
Medusa is a unified Managed Attack Surface Management (ASM) and SOC platform operated by SSO GROUP.
It continuously discovers digital assets, analyzes exposure, correlates threat intelligence, and delivers managed detection and response with audit-ready evidence.